As part of a hands-on project, I implemented Single Sign-On (SSO) for Amazon Connect using SAML 2.0 and Okta as the Identity Provider (IdP). My goal was to centralize user management and streamline access for agents, managers, and admins into Amazon Connect.

🔐 What I Set Up
- Configured the AWS Federation Application in Okta
- Created users, groups, and roles mapped to IAM permissions in AWS
- Defined trust relationships between AWS and Okta using SAML
- Used Okta’s SSO URL and Relay State to redirect users directly into Amazon Connect
- Learned to configure IAM roles with correct trust policies and SAML conditions
🧠 Key Concepts I Learned
- SAML Assertions: Secure XML documents issued by Okta that AWS uses to authenticate users
- SP & IdP roles: AWS acts as the Service Provider, trusting Okta to verify identity
- Audience URI (SP Entity ID): Tells AWS which service the assertion is intended for
- SSO URL: Initiates the login redirect to Okta
- ACS (Assertion Consumer Service) URL: Where AWS expects to receive valid SAML responses
🛠️ Tools Used for Troubleshooting
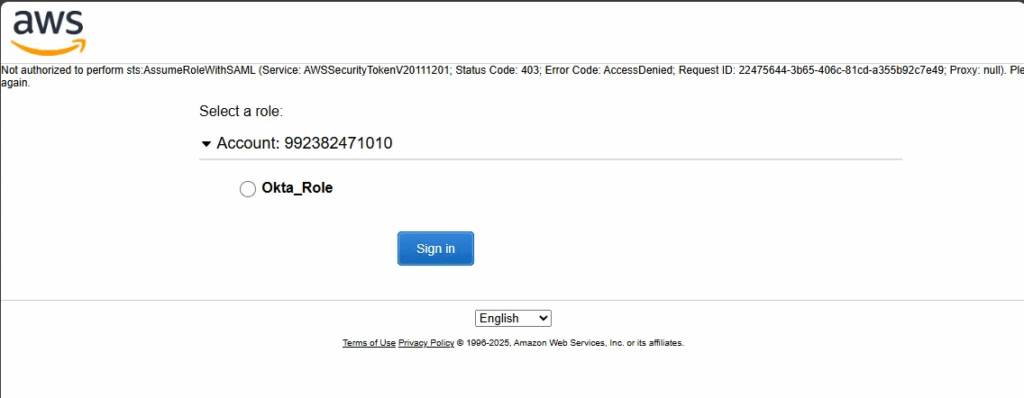
To debug authentication errors (like 403 AccessDenied or InvalidParameterException), I used:
- SAML-Tracer: A browser extension to inspect SAML assertions
- AWS IAM console to verify role trust policies and linked IdPs
- The AWS Okta + Amazon Connect workshop as a setup guide
⚠️ Real-World Fixes I Made
- Learned that mismatched audience URIs between Okta and AWS (e.g.,
urn:amazon:webservicesvshttps://signin.aws.amazon.com/saml/acs/...) can break the integration - Resolved errors caused by using an outdated IAM role or IdP in the trust policy
- Ensured proper attribute mappings in Okta to pass
email,firstName, andlastNameto AWS
✅ Outcome
With proper configuration and debugging, I enabled seamless SSO access to Amazon Connect. Users now authenticate through Okta and are automatically redirected into the right instance with no extra logins—secure, fast, and centrally managed.
